Recap: The attack that took the 5,500-mile Colonial Pipeline offline for four days back in May was one of the largest and most high-profile ransomware incidents in history. Now, the US State Department has announced it is offering a $10 million reward for information leading to the identification or location of those who lead the group responsible: DarkSide.
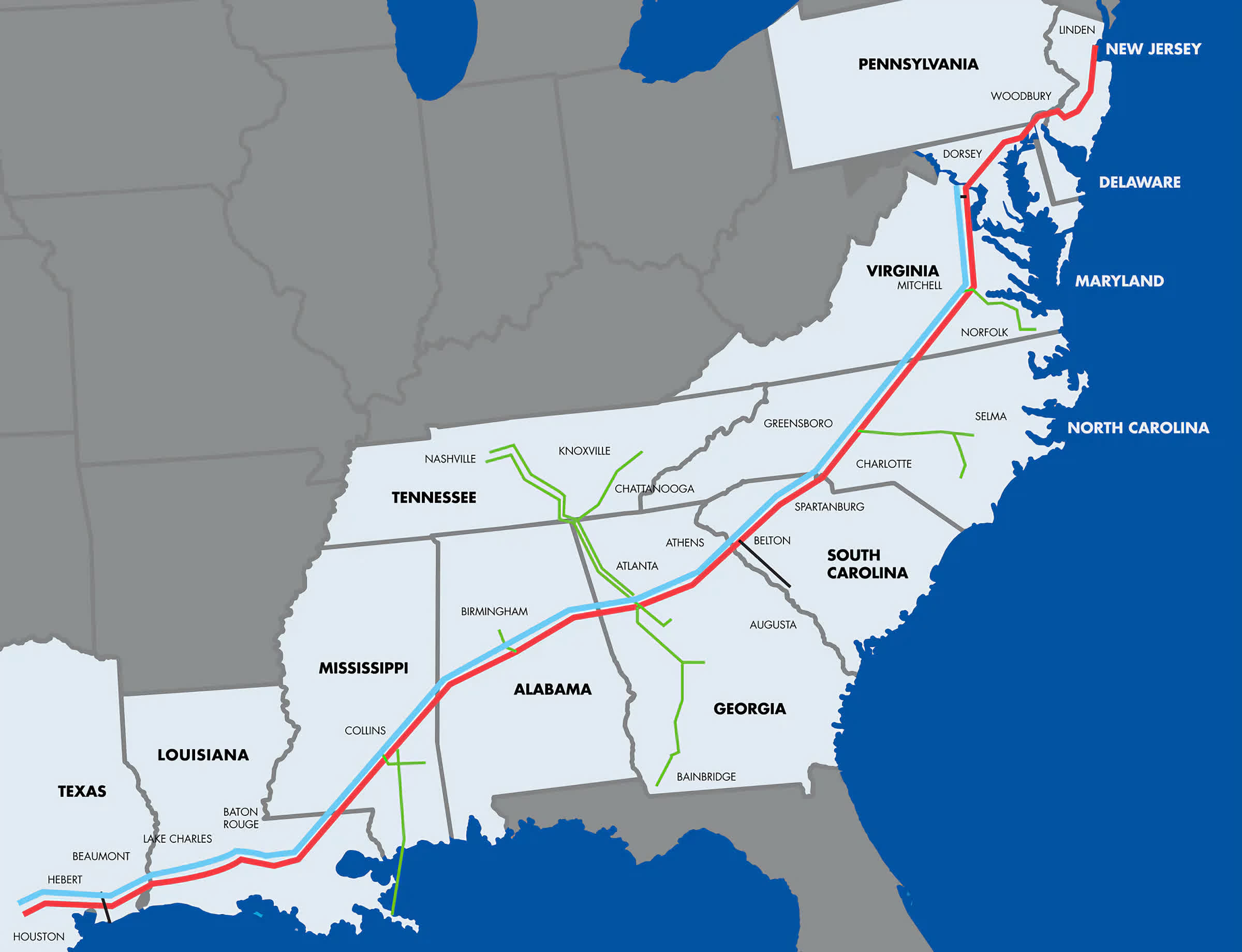
The Colonial Pipeline is the primary fuel line serving the US East Coast. It reaches over 5,500 miles and provides around 45 percent of the fuel needs of the region, so a ransomware attack on the operator that resulted in the pipe being shut down for four days was a major event. The attackers encrypted almost 100 gigabytes of the Georgia-based company's data, threatening to release it to the public if it didn't pay the ransom.
The attack led to fuel shortages in 17 states and Washington DC, panic buying, and concerns over how simple it would be for a foreign adversity to cripple vital US infrastructure. This is despite the group responsible, DarkSide, insisting the attack was solely about the money and that it didn't want to create "problems for society."
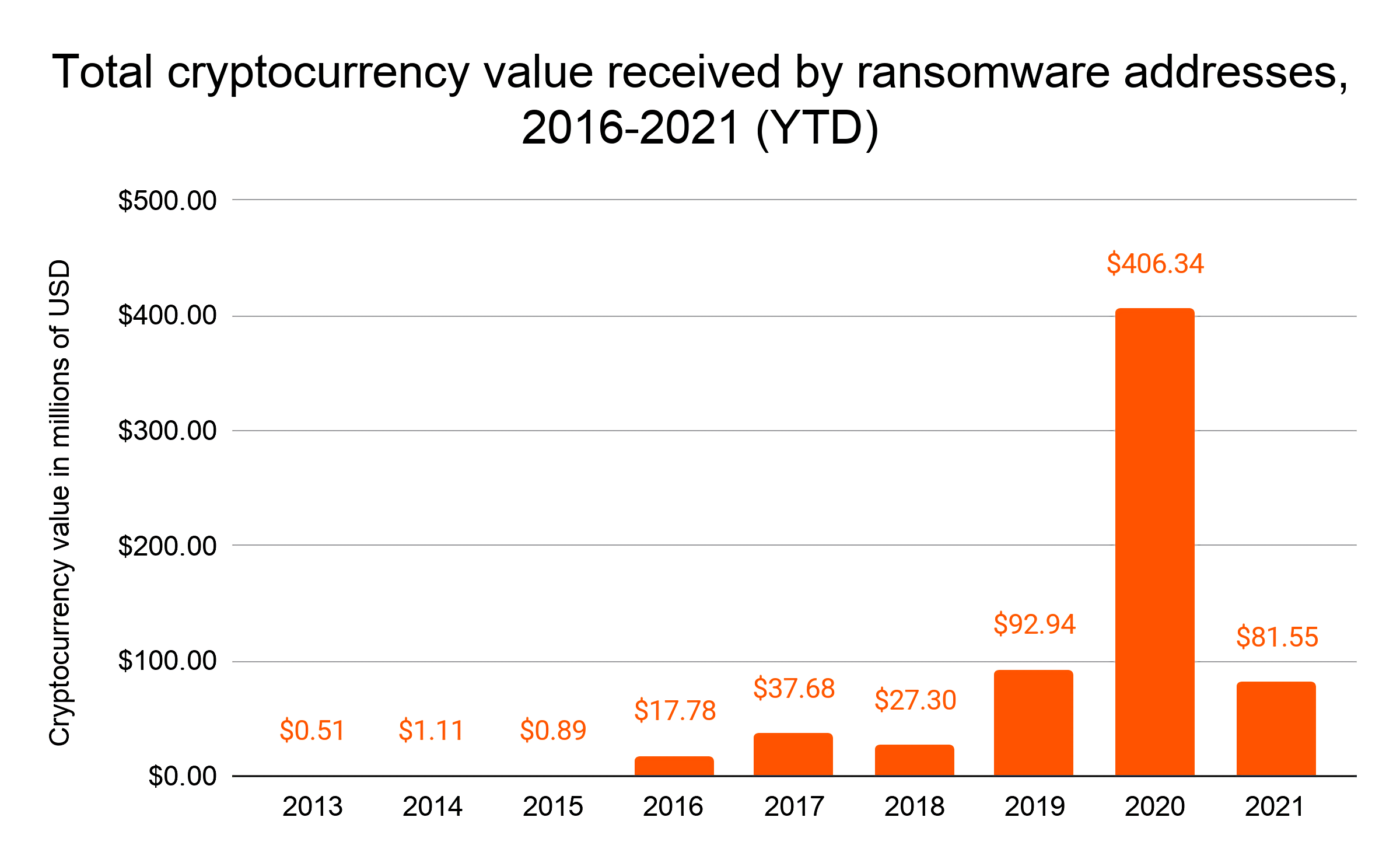
It was reported that Colonial paid 75 Bitcoin (around $4.4 million on the day of the transaction) in ransom to the Eastern European hackers, possibly using a cyberattack insurance policy.
The US Department of State is now offering $10 million for information leading to the identification or location of key DarkSide members. It will also hand over $5 million "for information leading to the arrest and/or conviction in any country of any individual conspiring to participate in or attempting to participate in a DarkSide variant ransomware incident."
DarkSide later apologized for the "social consequences" resulting from the attack. It also claimed it later lost control over its web servers and a significant part of its funds. The group stopped operating after the incident, though experts believe many members simply rebranded as a new entity called BlackMatter.
If you do have any information you want to hand over to the State Department, fire up your TOR browser and head to: he5dybnt7sr6cm32xt77pazmtm65flqy6irivtflruqfc5ep7eiodiad.onion.