In context: The cryptocurrency space has long been marred by Ponzi schemes, fraud, anti-consumer scams, and many rug-pulls and exit scams. With the advent of NFTs and blockchain games, the situation seems to be getting worse, with hundreds of millions evaporating from people who put their faith into these young and developing financial technologies.
Today, the developer behind a popular game called Axie Infinity announced that it suffered a serious breach of its Ronin cryptocurrency side-chain. The malicious actor used "hacked private keys" to break into Sky Mavis's Ronin validator network. The hacker stole no less than 173,600 ETH ($586 million as of writing this) and a further $25.5 million in USDC, a stable coin pegged to the US dollar's value.
This hack is not the first cryptocurrency heist, but it is easily one of the largest. It is bigger than the $611 million theft that occurred on the Poly Network in August 2021, one of the largest platforms for so-called decentralized finance.
For context, Axie Infinity is a play-to-earn game that relies on an Ethereum side-chain called Ronin for its reward system. To play Axie Infinity, one must buy at least three creatures called "Axies" and use them to earn "Smooth Love Potions." These can either be used to power up Axies or sold to other players. In short, users can trade ETH or USDC for "wrapped" versions they can use on a faster and more accessible blockchain to make in-game NFT purchases.
Axie Infinity has been heralded as one of the early success stories in the blockchain gaming space, as it managed to draw over 8 million players into its play-to-earn loop at its peak. The immense hype around the game has even allowed some players in the Philippines to turn a decent income by local standards. However, lately, the number of active players has declined significantly.
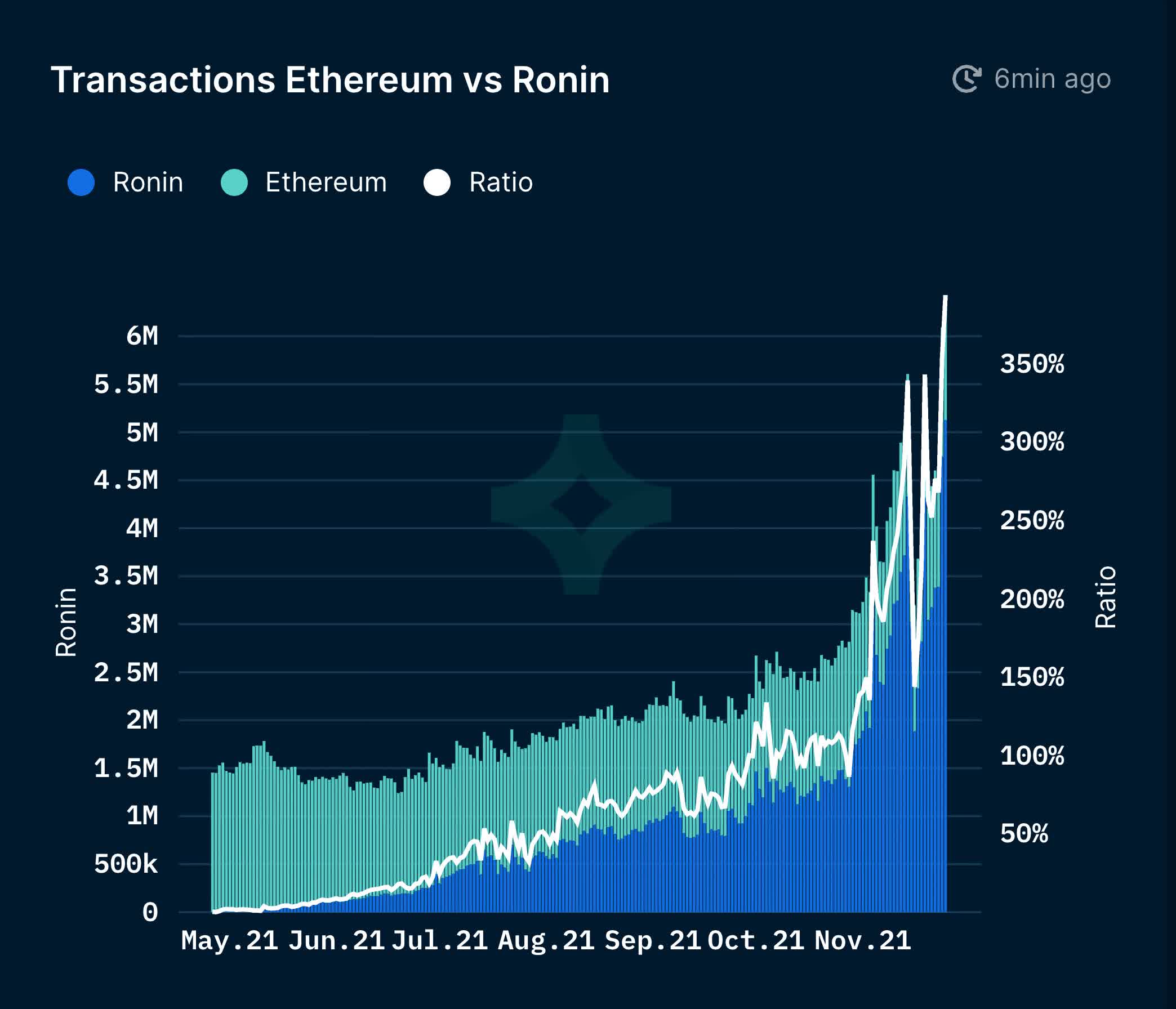
The problem that led to the hack was that side-chains like Ronin aren't as decentralized, as they rely on a so-called proof-of-authority system. In the case of Ronin, it is controlled by nine validator nodes that regulate transactions by staking their reputation. To achieve consensus on trades, five of them have to agree so that a deposit or a withdrawal can be authorized.
Sky Mavis manages four of those nodes, while third parties control the rest. In November 2021, Sky Mavis asked the Axie Decentralized Autonomous Organization (DAO) to help distribute free transactions due to enormous user demand. To that end, the Axie DAO placed Sky Mavis on an "allow list" so that it would be able to sign transactions on its behalf, a behavior that continued until December 2021.
As it turns out, the allow list persisted after that, allowing the attacker to gain majority control of the Ronin network --- in other words, the power to approve any transaction the bad actor wanted. While the attack took place on March 23, it was only discovered on Tuesday, when a user could not withdraw 5,000 ETH. By that point, the exploiter who used hacked private keys could forge enough fake withdrawals to go more than halfway on the road to being a billionaire.
This incident highlights the inherent risks present in Layer 2 solutions like the Ronin network. Ethereum's much-maligned proof-of-work consensus mechanism only allows for a relatively limited transaction capacity with high fees while consuming enormous energy to validate those transactions. Cross-chain bridges like the one built by Sky Mavis alleviate those issues but introduce a more elevated attack surface for hackers.
The company has paused the Ronin bridge to ensure no other fake withdrawals are made and is currently working with Chainalysis to monitor the stolen funds. It is also working with law enforcement and various government agencies to catch the person or group responsible for the attack and has promised that users will eventually get their funds back or be reimbursed.
The majority of the stolen funds are currently sitting in an Ethereum wallet. However, thousands of ETH have already been transferred to other addresses via exchanges, which means there's a chance they can be traced by those investigating the matter.
