In a nutshell: Security researchers at ThreatFabric have uncovered an Android banking-app malware called "Hook." The program allows hackers to take over a target's phone remotely. Bad actors can use it to steal data, exfiltrate personally identifiable information (PII), make financial transactions, and more.
A threat actor (TA), going by DukeEugene, sells the malware on the dark web and claims that he wrote the code "from scratch." However, TreatFabric's code analysis shows it to be a fork of Ermac, one of the most detected malware families in the wild. While most of the code is from the well-known banking trojan, the rest is bits and parts of other programs, showing there is no honor among thieves.
Despite DukeEugene's false claims of authorship (although the TA did write the original Ermac code), Hook brings many new features to the malware family. It includes WebSocket communication and encrypts its traffic using an AES-256-CBC hardcoded key.
What sets Hook apart from Ermac is its ability to use virtual network computing (VNC) to hijack an Android phone. The software can send virtual swipe gestures, scroll, take screenshots, and simulate keypresses, including a long press.
"With this feature, Hook joins the ranks of malware families that are able to perform full DTO [device take-over] and complete a full fraud chain, from PII exfiltration to transaction, with all the intermediate steps, without the need of additional channels," said ThreatFabric. "This kind of operation is much harder to detect by fraud scoring engines and is the main selling point for Android bankers."
The researchers say that Hook also acts as a file manager. Hackers can use it to view all files on the phone or download any they find valuable. It can also view or download any images on the phone. Hook doesn't even need to use shell commands to perform file exfiltration. Instead, it uses existing Android APIs to steal the files. This capability coupled with its access to real-time GPS tracking information makes it a dual-duty banking-trojan/spyware suite.
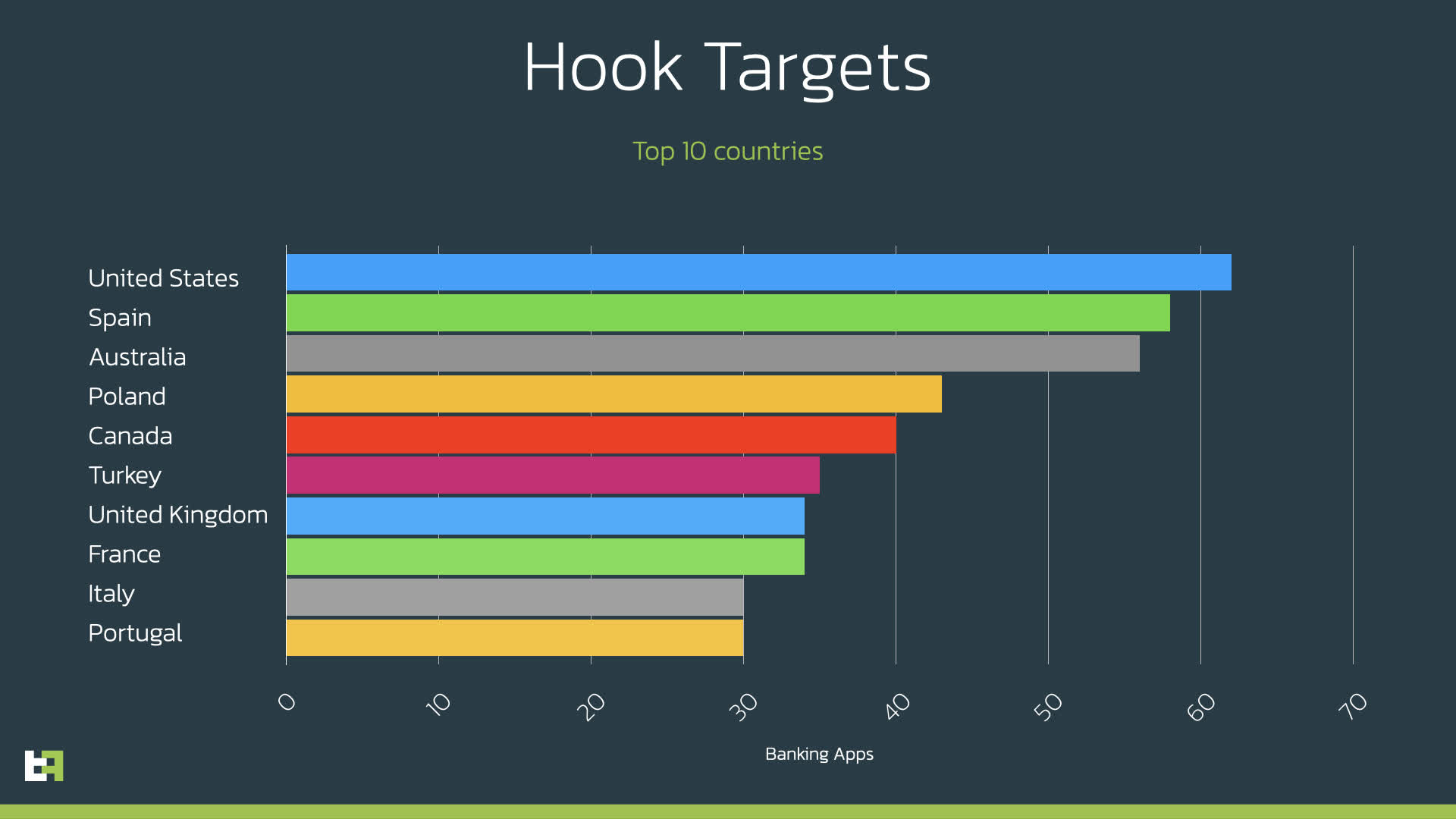
The malware's victims (banking apps) are widespread and extensive, with the US, Australia, Canada, the UK, and France all reported in the top ten of targets. However, ThreatFabric says that the list of countries outside the top ten is wide-sweeping, with those regions only slightly lower than tenth place. The researchers posted a complete list of targeted apps and the package names associated with Hook at the end of their blog post. The article also has all the technical nuts and bolts for those interested.
As to mitigation, always practice safe security hygiene. Avoid downloading software outside of the Google Play Store or other trusted sources. Since Hook relies on Accessibility Services permissions to function, be wary of apps asking for that type of access.
Image credit: ThreatFabric
